PC Plus HelpDesk - issue 263
 |
This month, Paul Grosse gives you more
insight into some of the topics dealt with in HelpDesk.
|
 |
HelpDesk
|
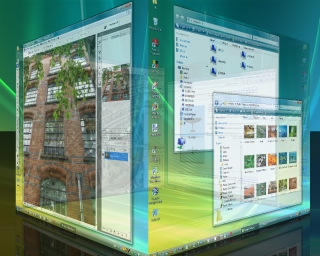 However, it is not all bad news for Windows
users. However, it is not all bad news for Windows
users. There are some 3D cube-style plug-ins for Windows (these are plug-ins) and the one featured in the screenshot is "Yod'm 3D". It works similarly to Beryl - you can configure the shortcut keys in a similar way - but because it runs as a different layer to the Aero interface, as opposed to instead of it, it is rather sluggish in some instances (this is on the same machine that runs Beryl smoothly). However, if multiple desktop organisation on Windows is your aim, this is just what you need. At the moment, it is free (there are plenty of mirrors listed on Google) but OTAKU software has taken it over and the new version, called 'DeskSpace', will lighten your wallet. One advantage of this program is that it is a stand-alone that does not need to be installed - you just run it from the directory you expanded the .ZIP file into. There are others - 'cube desktop' (http://www.cubedesktop.com/) for example - use the one you feel happiest with. |
|
Load files from anywhere
The screenshot shows Notepad running on Windows Vista but the same applies with text editors running under various flavours of UNIX as well. If you are running the KDE window manager, you have the luxury of many different kioslaves to do the work as well. All you need to do is click on 'File', 'Open' and then type in the protocol ('http://', 'ftp://', 'smb://') along with the rest of the URI, exactly the same as you would in a browser address bar. In the screenshot, you can see the BBC's site's robots.txt file - this tells spiders where not to look. The only difference you might find between doing this on Windows and UNIX is that often, web files are stored in UNIX format which NotePad does not understand - you end up with a single line of text instead of separate lines. Remember though that one thing you cannot do - unless you have the appropriate rights - is save the files back to the server that supplied the file. |
MAC addresses
Network communications rely upon MAC addresses being
unique and they appear to be random. However, that is not
the case at all. |
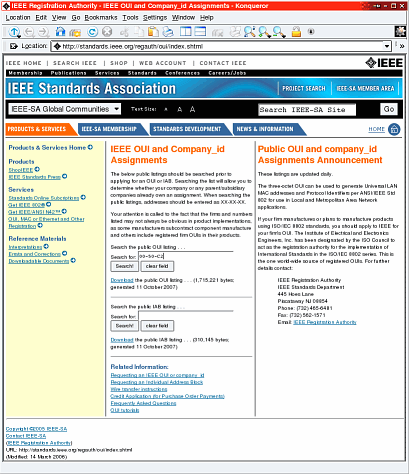 The first six nybbles (a nybble is: 4 bits;
half a byte; or, a hex digit. Also note that 'nybble' can
also be spelled 'nibble') of the MAC address (the
'Organizationally Unique Identifier' or 'OUI') identifies
the organisation that produced the NIC. These are large
organisations that produce thousands such as Xerox and
Cisco ('00-03-FD-' amongst others). However, not every
producer needs such a large address block. The first six nybbles (a nybble is: 4 bits;
half a byte; or, a hex digit. Also note that 'nybble' can
also be spelled 'nibble') of the MAC address (the
'Organizationally Unique Identifier' or 'OUI') identifies
the organisation that produced the NIC. These are large
organisations that produce thousands such as Xerox and
Cisco ('00-03-FD-' amongst others). However, not every
producer needs such a large address block.The smaller companies have a special block called an 'Individual Address Block' or 'IAB' which allows up to 4096 devices. These start off with six nybbles ('00-50-C2-') and then the assigned range, for example, Microsoft's IAB range is '00-50-C2-00-30-00' to '00-50-C2-00-3F-FF'. You can use a MAC address to identify the manufacturer
by typing it into http://standards.ieee.org/regauth/oui/index.shtml
. Remember that if it starts off with '00-50-C2-', it is
an IAB. |
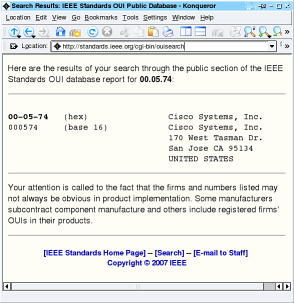 On Windows, you can find your own MAC
addresses by opening a console and typing 'ipconfig
/all'. On UNIX, you have to log on as (or su to) root,
then type 'ifconfig -a' - On Windows, you can find your own MAC
addresses by opening a console and typing 'ipconfig
/all'. On UNIX, you have to log on as (or su to) root,
then type 'ifconfig -a' -this is because ifconfig requires privileges as it is a powerful command that can affect other system users. |
Converting PDF to ASCIIWe all know that you can create PDF documents directly from all of the best word processors but this seems to be a bit of a one-way journey. Suppose you have exported your file to PDF and then your machine has crashed or there is some other reason why you only have a PDF version and no version that your word processor can import.
On Linux, there is a utility called 'ps2ascii' that uses the Ghostscript (PostScript and PDF language interpreter and previewer) engine. It will convert PostScript ('.PS') or Portable Document Format ('.PDF') files into ASCII. It ignores formatting so, as you can see in the screenshot, the tiny text - 'This is small text...' - is converted just the same as the larger text. All you need to do is pass the name of the PDF file to the program and it will output the text as ASCII to STDOUT - usually the console. If you specify the name of a text file, it will save it as that. With a lot of PDF files, you could easily write a shell or Perl script that globs the relevant file names and then saves each file's ASCII content as a separate file with the same name but with the '.TXT' extension, ready to parse and catalogue. |
|
Memorable Hex KeysIf you have a number of computers to input WEP keys for, don't want to do anything other than type them in manually (most secure) but don't want to write them down (even more secure) there are ways of producing keys that you can remember. However, you must also remember that by doing so, you can make them a little less secure because they become vulnerable to a modified dictionary attack. Still, here is how to do it if you are interested in trying it out, or are morbidly curious. Hex digits represent nybbles so, for a 104-bit WEP key, we need 26 values between '0' and 'F'. Choosing randomly produces fairly secure keys but you need to write them down if typing them in manually - pieces of paper get lost or copied. So, how can we make 26 nibbles more memorable? One solution uses words from existing letters and substitutions - look at the Perl program by clicking here (both a UNIX version and a Windows (.PL) version, together with a dictionary from words consisting of the letters 'oizwhysglpabcdef' that you can play around with. All good operating systems come with Perl by default. For the rest, you can get it from 'ActiveState'). Hex uses the letters 'a' to 'f' which is rather limiting - 77 words including some dodgy ones. If we substitute numbers with letters, we can go further. Using a '1' as an 'i' and a '0' as an 'o' gives 264 words and, adding a '2' and a '5' as a 'z' and an 's' gives us 871 words. A '6' looks a little like a 'G' giving 1,185 words but there are still gaps.
Rotating '3' gives a 'w' (we already have an 'E' so making that from a '3' is redundant) and mirroring '9' produces a 'P' giving 6,188 words, leaving just '8' unused - make up your own. Also included below are possible calculator words... |
||||||||||||||||||||
|
||||||||||||||||||||
| There are no fixed substitution rules. |
||||||||||||||||||||
|
||||||||||||||||||||
However, remember your security and the
simple rule 'big polysyllables disallowed' or
'b1690745477ab7e5d15a77o3ed' because it makes it too easy
to crack. Using words that are too long allows for
dictionary attacks on your keys (instead of gazillions of
unrelated hex character combinations to choose from
(taking many times the life of the Universe to break),
they have a relatively extremely limited selection of
words to choose from).
Have fun. |
||||||||||||||||||||
 Beryl on Windows?
Beryl on Windows? Vista - How much RAM?
Vista - How much RAM?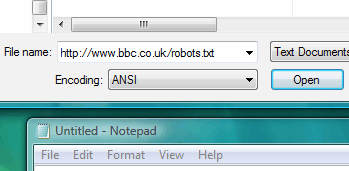 If you
want to load a flat text file such as plain text, HTML,
XML, SGML and so on, from a server, you can do it
directly into the text editor itself.
If you
want to load a flat text file such as plain text, HTML,
XML, SGML and so on, from a server, you can do it
directly into the text editor itself. If you have
a half-decent firewall, you will get emails telling you
about IP-Spoof attacks from certain MAC addresses (such
as the one on the right). The MAC address (six
hexadecimal pairs identifying the Network Interface Card
or 'NIC') is only really of any importance if you have
access to the same physical subnet as that interface
(which is why it is important with IP spoofing).
If you have
a half-decent firewall, you will get emails telling you
about IP-Spoof attacks from certain MAC addresses (such
as the one on the right). The MAC address (six
hexadecimal pairs identifying the Network Interface Card
or 'NIC') is only really of any importance if you have
access to the same physical subnet as that interface
(which is why it is important with IP spoofing).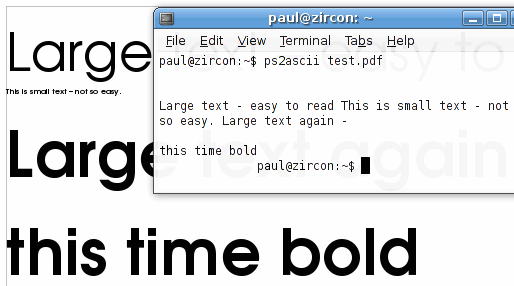 This task
isn't as difficult as you might expect it to be.
This task
isn't as difficult as you might expect it to be.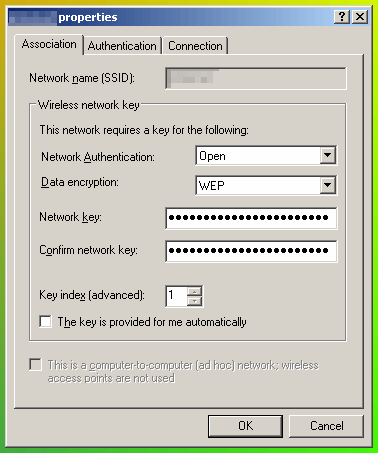 WEP Keys
WEP Keys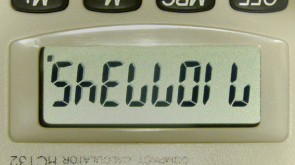 If you
type '71077345' into a calculator and invert it (when I
did my A-Levels we were about the first year that were
allowed to use calculators - no memory or even a per cent
button), you get 'SHELLOIL' so we'll use a '7' and a '4'
as an 'L' and a 'h' (optionally a 'y'), giving us 3,757
words from which we can make sentences such as; 'diseased
dodo seizes cafe food' which translates to
'd15ea5edd0d05e12e5cafef00d'.
If you
type '71077345' into a calculator and invert it (when I
did my A-Levels we were about the first year that were
allowed to use calculators - no memory or even a per cent
button), you get 'SHELLOIL' so we'll use a '7' and a '4'
as an 'L' and a 'h' (optionally a 'y'), giving us 3,757
words from which we can make sentences such as; 'diseased
dodo seizes cafe food' which translates to
'd15ea5edd0d05e12e5cafef00d'.