PC Plus HelpDesk - issue 222
This month, Paul Grosse gives you more insight into
some of the topics dealt with in HelpDesk and HelpDesk
Extra
|
 |
HelpDesk
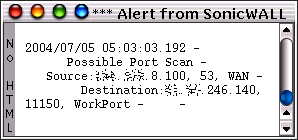
Being attacked by your DNS?Unless somebody has actually managed to break into your ISP's DNS and is using it to mount attacks on its customer's, it is more likely that somebody is trying to attack you directly. Why? Well, life it too short to be everybody else's psychiatrist. But, this is how it is done. Many (you might like to think of that as reading 'A few') home users will have desktop firewalls on their machines and some of these firewalls will be of the type that will look at a port scan and decide at some stage of the attack, that all traffic from that IP address is hostile. If it does, the usual course of action is to block that IP address so that the firewall can carry on doing what it is supposed to do. Many home users will log onto their ISP and get a dynamically allocated IP address so if an attacker wants to change IP address, all they have to do is log off and then log on again (there are other ways of doing it but that is the simplest in most cases - 'switch off, switch on'). Recognising this, the firewalls will not (usually) block a particular IP address for more than a certain amount of time (say, 500 minutes, aka 8 or so hours). This way, genuine users that have inherited a 'bad' IP address, will not be blocked for ever which can only be a good thing (it is conceivable that the attackers could eventually write-off a whole IP address block if they were labelled permanently).
This can be done by doing a port scan or some other attack but instead of having the attacker's IP address as the source address, they substitute your DNS's IP address(es). Your firewall sees the attack and blocks off all traffic in both directions to the DNS and before you know it, you cannot convert the domain name into an IP unless it is stored locally. To combat this:
Choose your poison. That is, of course, if you only use your own ISP's DNS servers. There is one way that will get around this problem completely. If you have your own ISP's DNS servers as the top servers in the list, they will get all of the requests as they should. However, if you include some other DNS servers, these will (if they are configured to allow you to) replace the service until your firewall will let the others online again. |
Automatically downloading the web with wget.If you don't want to sit up at night, waiting to download your webcounter at a specific time, making sure that you never miss one, even when you are on holiday, you need to automate the process. Linux
# wget the fast counter image on Fridays and Sundays
# and put the image and the log in the /home/paul/wget/ directory
#
59 23 * * 5 paul wget --proxy=off http://counter.uri
-P /home/paul/wget -a /home/paul/wget/fc_log
59 23 * * 0 paul wget --proxy=off http://counter.uri
-P /home/paul/wget -a /home/paul/wget/fc_log
1 0 1 * * paul wget --proxy=off http://counter.uri
-P /home/paul/wget -a /home/paul/wget/fc_log
(Note that each line in the crontab file other than the comment lines begins with the time data and that in the real file, the line beginning with '-P' is a same-line continuation of the above line displayed here, ie '-P' comes after the counter URI.) In the above crontab listing, the lines execute wget as user 'paul' at 25:59 every Friday (5) and Sunday (0) and at one minute past midnight on the first day of every month. Windows
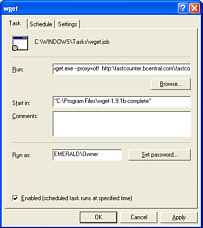
Unfortunately, Windows is not blessed with an easy-to-use crontab file. Instead, we have the scheduler which can be found under Start/Programs/Accessories/System Tools/Scheduled Tasks. Instead of just adding a line or two to a file, we have to work out way through a wizard, eventually finishing with the desired result. Click on the image on the right to see it full-size. |
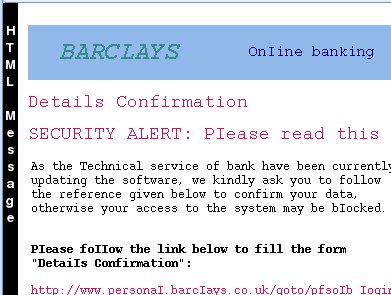
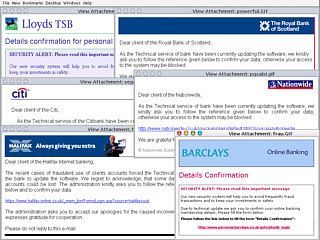
PhishersPhishing is a social engineering attack and, if the figures are to be believed, it has a very high success rate with around a quarter of recipients believing what they see. They come in a number of guises in html mail with or without images. Either way, they need to convey the impression that they are the genuine article but send the victim off to some site other than the one that they think they are going to. To do this, they either have an image that looks like a web page but instead of just the part of the image with the link being active, the whole image is active, or, they use an innocent looking link. In both cases, the user thinks that they are clicking on one thing when in fact, they are being mislead. In html text links, the apparent link can be different thus: <a href="http://bogus_site.com/" >https://okay_site/innocent_login.html</a> which will look like this... https://okay_site/innocent_login.html If you hover the mouse over the link, you will see that the real URI appears in the left part of the status bar of your browser (if you have it turned on). This can be overcome with scripting and other browser-specific methods so that it appears that the correct URI is being pointed at. Also, there are ways of getting browsers to display the secure (padlock) icon as well. Text onlyText only phishing scams will get mail browsers that have images turned off but have to get past anti-spam programs. In the example below, you can see how this is done (although not successful in this case).
In this case, all looks all right until you look a little closer at it.
If that is not enough to convince you, I then highlighted it merely by dragging the mouse across it and got the following...
You can now see all of the text that was written in the same colour as the background - it is the text that appears on the same coloured background (dragging the mouse across it swaps the colours around the new background is the old text colour and the new text colour is the XOR of the old text colour so white text on white background becomes black text on a white background and so on). The spammer/phisher uses this to try to get it through the spam filters by making it look like text that the spam filter does not recognise. ImagesImages, of course, cannot (yet) be analysed by text monitoring software such as spam filters. These usually appear as an attachment in a very sparse email that is little more than a link in the image (the whole image). They look like the collection below and if you click on the image, you can see a full-screen montage in a new window. As you can see, the images have random names. All the phisher has to do is to set up a server, steal the images from the bona fide website and get working. Soon, (s)he will have people's account details. All the user can do is refuse to co-operate with such requests. Banks know that this route to resetting a user's account (if it ever did need doing) is not usable and will not ask you to participate in this. So, don't. |
HelpDesk Extra
Computer Modelling:Last month, we looked at the humble spreadsheet and saw how to do double entry book keeping using only one function. Here, we take it a little further and make an outright computer model, but again, if you look at the files on the SuperDisc, you will see that the number of functions that have been used is very small. Thrown object ballistic flight computer modelComputer modelling is a lot easier than you would think. Although I have been up to this since before Chernobyl I still think that it is fairy easy for any people who can apply themselves to it. My first computer model was for a counter-current heat exchanger that I was going to use as part of a model for a nuclear power station game that I was writing. I had got all of the cooling circuits, exchangers, pumps and everything working fine and then Chernobyl happened so that was the end of that. My second was for a chemical company I later got a job with. I modelled a chemical reactor and local plug-reaction circuit and immediately unearthed a fault in the programme logic control sequence - correcting it saved the company around 30,000 GBP per year. Since then I have modelled all manner of things - go to Google and look up 'water rockets'. However, easy though it might be, it is even easier to make mistakes. If you have gone straight to computer program, it will be very difficult to track down. But, with a spreadsheet, you can take each time slice and allocate it a new row. In these cells, you can see if any value is oscillating wildly or expanding exponentially. It is all very visible. And here are the files you can use to see the model described in this month's PC Plus magazine in a number of popular file formats. Note that the OOo file will open in Linux as well as Windows (or any of the other supported operating systems). Once you have a working spreadsheet model, you can get down to programming it in your favourite programming language. |