PC Plus HelpDesk - issue 211
This month, Paul Grosse gives you more insight into
some of the topics dealt with in HelpDesk and HelpDesk
Extra
|
 |
HelpDesk
LAN IP AddressesRangesInternet IP addresses (apart from the experimental ones) run from 1.0.0.0 to 223.255.255.255 with a few holes for special reasons. Whilst it is nice to have Internet access on a LAN, there are usually a few devices that do not need to see the Internet - printer servers and so on - so it would no only be wasteful if everything that was on your LAN has its own Internet IP address, it would also be an immense security risk. Supposing you had 12 IP addresses - a few servers that were only for LAN use, a few network printers and so on amongst a population of computers. If you had Internet addressable IP addresses for each when only a few of the computers actually needed to venture onto the Internet, then people from anywhere on the planet would be able to interrogate your network server or your printer and so on. It would also use up the available IP addresses very quickly. With this in mind, this is where local addressing for LANs comes into its own. If your gateway knows that a certain range of addresses are never going to be found on a particular connection it can then keep that traffic away from that connection. In this way, a local addressing scheme is used so that machines that can function perfectly well without any interaction from the Internet can do so. For a class 'A' LAN, you can start your network with 10 in the first octet (eight bits) of the address and the gateway will not pass connections to these machines out onto the Internet (ie 10.x.x.x). For a class 'B' LAN, use the range 172.16.x.x to 172.31.x.x and for a class C network, use addresses in the range 192.168.x.x. This is why LAN cards for domestic use say use the IP address 192.168.0.1 or 192.168.1.1 for the machine (usully because the person installing it is doing it for the first time so there won't be any other addresses on the network at that point and when there is, they will have figured out enough of what is meant by then to experiment a bit and get it right). There is nothing (usually) to stop you from using class B addresses on your LAN if you really want to. Subnet MasksYou will notice that the IP addresses for class B and C LANs both change in the third octet but the subnet masks are not the same. For a class B network the subnet mask is 255.255.0.0 and a class C is 255.255.255.0. This means that on the face of it, you can have a network range of, say for a given network, 172.21.0.0 to 172.21.255.255 for a class B and 192.168.15.0 to 192.168.15.255 for a class C. You can see that for a given LAN, you have 256 times more addresses to play with on the class B network. Of course, you don't get all 256 addresses to play with as 0 (as in 172.21.0.0 or 192.168.15.0 in the above examples) is the network address and is used in a particular way by the system and, there is also the broadcast address which normally has all of the network address, non-subnet mask bits set to 1 so for a class C, that is 255 and for a class B, that is 255.255 (as in 172.21.255.255 or 192.168.15.255 in the above examples). To get the network address, you need to take the IP address and AND it with the subnet mask. Thus the example of 192.168.15.26 ANDed with the subnet mask of 255.255.255.0 will give 192.168.15.0 as the network address. If the gateway ANDs the IP address with the Subnet mask and gets your internal LAN network address, it will not pass the traffic out onto the Internet or into the next network. It is also useful in some instances, such as where you have a busy internal network, to have such a gateway or packet filter (first generation firewall) next to the firewall so that the firewall does not have to bother investigating internal traffic and can concentrate on looking at the traffic you bought it for. Looking at it all graphicallyTo make all of this clearer, lets look at it graphically...
A host address such as this is sometimes written as 192.168.1.15/24 You don't have to use a whole octet of 0s for your subnet mask. You could have 255.255.255.240 which would give you a network with 13 hosts and a gateway like this...
This host address could be as 192.168.123.150/28 You can make this interesting because, you might find that you do not have to have the end of the subnet mask as a contiguous block of zeros. If you still need around a dozen (or 13) machines and the network needs a network address, a broadcast address and a gateway address (ie 16 addresses in all which, being binary, can be represented by 4 bits) you might find that it doesn't matter if they are contiguous. If there are 4 bit-sized holes in the subnet mask, you can have your 16 addresses as long as the first section of the address remains intact. Supposing your subnet mask was 255.255.255.149...
So, the valid numbers in the last octet for this hypothetical network are:
Forget about using the slash notation with this as it becomes nonsensical. Note that where a subnet mask bit is set, the network address bit stays the same in the host address. If you are going to have a go at setting up a small network like this, make sure that you have plenty of time to get it working again should there turn out to be a problem with it for some reason. Also, note that DHCP servers like to have contiguous IP address blocks to assign numbers to so you might find that it does not work with your DHCP server. It could be that your DHCP server uses the subnet mask to check for valid suggestions but it might well not. Remember, you will never know unless you have a go. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Make your own EICAR test fileClearly, we couldn't include this on the SuperDisc as a ready made executable file because your anti-virus program would pick it up and not allowed you to do anything with it. Further than that, it could be that some AV programs would then not allow you to access any part of the disk (because it is a removable medium) and that would not be on. So, here is how to make the file which,
Trying to execute this file will cause any on--access AV product detect it and, if it is working properly, not allow you to run it. Also, if you scan where you have saved the file, your on-demand scanner should pick it up and do likewise. If you can run it, it just opens up a DOS box and prints the string EICAR-STANDARD-ANTIVIRUS-TEST-FILE! Here is how to make it.
Note that not all AV programs are programmed to detect this but most should. If yours doesn't either it is not configured properly or it is not programmed to look for the test file. X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H* If you change the name of the file (remembering to leave the extension as a .com of course) it will still detect it. |
HelpDesk Extra
Starting OpenOffice.org office programsWith OpenOffice.org office programs, it is possible to
try them out in Windows in order to get used to them. Once you have installed the office suite, you can opt to have it load from the system tray on the Taskbar - here under Windows XP. This is a lot quicker than going through the Start menu. For this Helpdesk Extra, we are looking at using the Drawing program. |
Toolbars and Tools
If you put the mouse over the Visible Buttons menu option, all of the buttons that are available in that particular toolbar are displayed, again with ticks by the ones that are displayed.
If you hold down the mouse over one of these, another menu is displayed and you can select one of these which will also be the default the next time you click on there. Tool-tips are also useful while you are familiarising yourself with the interface. |
3D Effects
Really, the only way to familiarise yourself with the
functions available with this is to have a play around
with it.
You can download this from the Internet to play around
with yourself. Being a vector graphics image, it is
resizable without getting any step patterns in diagonal
borders as you do in pixel image files such as BMPs and
so on.
Being 3D now, you can rotate him and although he is
not particularly penguin shaped from other angles, you
can see how the shapes interact with and intersect each
other.
|
LightingNormally, objects - including the Windows interface - are lit from the left. That is just the way that it is normally. In our case, the WMF of Tux is lit from the right so it is important to light any 3D models that we create from the right as well otherwise they will look out of place. Often in films, you can see when somebody is superimposed on a background, not necessarily from any line around the actors (as it is possible to get rid of this these days) but from differences in the way that the actor and the background are lit. There are a number of clues such as:
Get any of these wrong enough to notice and you don't stand a chance.
|
Transparency v GradientsA gradient goes from one colour to another and for the back of an image, this is all right. However, if you want to overlay another colour, going from, say, black to white as in a shadow, it will obscure the background image. If instead, you make the shape a solid colour and have a gradient transparency, you can still see the background image.
Transparency can also be used in images that support it such as vector images like WMFs and other metafiles and also in images such as PNG or GIF. With PNG where the transparency is in the form of an alpha channel, this can make the degree of transparency variable so if you wanted to generate an image of, say, a lens flare, you could do this in, for instance, the GIMP, save it as a PNG and then use it in OpenOffice.org Draw. |
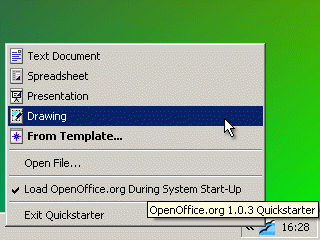 If you want to stay
with Windows, that is all right but if, in the long term,
you are planning to move over to Linux, or one of the
other supported operating systems, it is a useful
starting point as all that the users will have to get
used to when you change operating system is the system
itself and for those of us that use Linux with, say, KDE,
there is not a greate deal of difference any way as far
as the end user is concerned.
If you want to stay
with Windows, that is all right but if, in the long term,
you are planning to move over to Linux, or one of the
other supported operating systems, it is a useful
starting point as all that the users will have to get
used to when you change operating system is the system
itself and for those of us that use Linux with, say, KDE,
there is not a greate deal of difference any way as far
as the end user is concerned.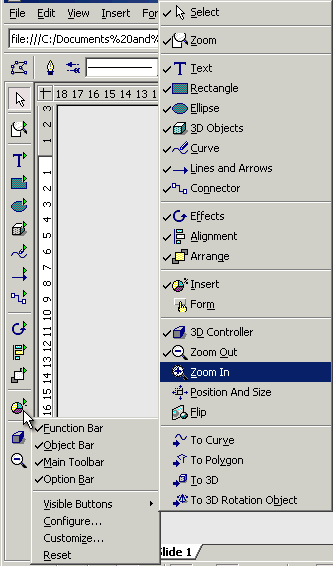 If you right-click on
any of the toolbars, you will get the smaller menu,
displaying which bars are displayed. Put a tick by any
that you want.
If you right-click on
any of the toolbars, you will get the smaller menu,
displaying which bars are displayed. Put a tick by any
that you want.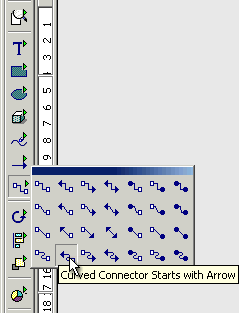 Some of the toolbar
buttons have a green arrow as part of the design.
Some of the toolbar
buttons have a green arrow as part of the design. The 3D Effects dialogue
box appears when you press this innocent looking button.
The 3D Effects dialogue
box appears when you press this innocent looking button. The original Tux
Windows Metafile.
The original Tux
Windows Metafile. Tux turned 3D and
then grey (instead of the default pale blue)
Tux turned 3D and
then grey (instead of the default pale blue)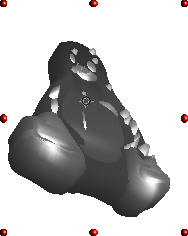 Note that this
program is a vector drawing program with 3D facilities
and not a 3D modeling program per se. Therefore, if you
create several 3D objects separately and overlay them,
they will only go one in front of the other, they will
not occupy the same space. It is as though the 3D image
for each is converted into a 2D image and it is these
images, one for each 3D object, that are overlaid.
Note that this
program is a vector drawing program with 3D facilities
and not a 3D modeling program per se. Therefore, if you
create several 3D objects separately and overlay them,
they will only go one in front of the other, they will
not occupy the same space. It is as though the 3D image
for each is converted into a 2D image and it is these
images, one for each 3D object, that are overlaid. In the image on the
right, the upper set of objects look as though they
belong to each other because the lighting is consistent
whereas the lower set do not because they are lit from
different directions and with different coloured lights
In the image on the
right, the upper set of objects look as though they
belong to each other because the lighting is consistent
whereas the lower set do not because they are lit from
different directions and with different coloured lights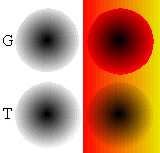 In the image on the
right, the top shades use gradients to effect the
transition from black to background colour. This is fine
with the one on the left and if the background on the
right was a continuous red, it would work okay as well.
However, because the background is a gradient, a simple
gradient for the image in the foreground is not good
enough. The lower pair of shades use transparency with a
solid colour (if you really wanted to, you could use a
gradient here as well if the effect suited your needs)
and as you can see, the shading works regardless of the
background.
In the image on the
right, the top shades use gradients to effect the
transition from black to background colour. This is fine
with the one on the left and if the background on the
right was a continuous red, it would work okay as well.
However, because the background is a gradient, a simple
gradient for the image in the foreground is not good
enough. The lower pair of shades use transparency with a
solid colour (if you really wanted to, you could use a
gradient here as well if the effect suited your needs)
and as you can see, the shading works regardless of the
background.