PC Plus HelpDesk - issue 210
This month, Paul Grosse gives you more insight into
some of the topics dealt with in HelpDesk and HelpDesk
Extra
|
 |
HelpDesk
Securing Your Computer
Many people talk about firewalls (especially firewall
vendor websites) as though they will secure your networks
completely. Yet, there is a totally secure option that
you can use at least part of the time if you don't trust
your firewall completely - certainly if you want to leave
it while you go out to the shops or to bed at night. When
not using this solution, you should, of course, use a
firewall of some sort. Start the mpeg below by moving the
mouse over it
|
Password AttacksPasswords are usually encrypted using something called a 'trapdoor algorithm'. This makes a meaningless string from your password and it is not reasonably feasable to calculate your password from the result - it is far easier to take a word or some other string that you suspect to be a password, put that through the same algorithm and see if you get the same result. Passwords themselves have a problematic history: they have suffered from a number of things including incompetent strategies for selecting them. The date is often used when a password is changed daily or worse still, the word 'today' was used by one company. Many people choose words from the dictionary but these are subject to an attack where every word is put through the algorithm. When a password is in the order of eight characters long, it makes life easier to crack it by looking at the words in the dictionary as there are far fewer of them than there are combinations of letters of the alphabet for a given length. Another strategy is to put two words together and possibly add a non-alphanumeric character between them - 'pencil<tractor' as an example - or to take a word and insert an non-alphanumeric character into it - 'the8atre'. Some people thing of substituting certain letters with other characters so 'Biggles' becomes '8i99le5'. However, password cracking algorithms try all of these as well (I've seen it demonstrated). The brute-force attack tries out every possible combination of all of the characters used to make passwords. If you use just lowercase characters - a to z - there are 26 possibilities for each character in the password. If you use a mixture of upper and lowercase then there are 52 possibilities. Add in the numbers and you have 62 and when you add things like @~#[]{}()<>!£$%^&*-+=, you are starting to make things difficult to guess. As far as the length of passwords is concerned, the longer the password, the harder it is to crack with brute-force. If, for example, you use just upper- and lowercase characters and numbers, a one character password will have 62 possibilities and with brute-force, you will have to go through (on average) half of them to get a success. With two characters you will have 62^2 possibilities or 3,844. With three, you have 238,328 and so on. With eight characters, it is fairly secure (218,340,105,584,896 combinations). With root password strength, (85 different characters and creating a password 12 characters long), you are talking of 142,241,757,136,172,119,140,625 combinations. With around 40,000 words in everyday use in English, you can see that even a three character such as 'hR6' or '8Jy' is more secure than using a word such as 'people' or even 'pressurisation'. With this, we start to get into the realms of how long it takes for a computer to crack a password. If a computer can go through the trapdoor algorithm 1,000 times a second and, on average, it requires half the passwords tried to get a match, a 3 character password (taken from 62 choices for each character) would take just over half an hour to crack. An 8 character password would take nearly 3,500 computer years to crack (on average). Root password strength would take 2,253,684,645,476 computer years (or 187 times the age of the Universe - one large parallel computing operation). Keep in mind that distributed systems such as Seti@Home have managed to clock up millions of years of computer time and that if a security agency was serious about cracking your password, they would be able to do substantially more than 1,000 attempts per second. Another thing to think of is that although a complicated password is difficult to remember, it is even more difficult to guess. Having a difficult password and taking care of it - never compromising it - can be more secure than having passwords that are easier to crack changing more frequently. However, no amount of clever testing though will counter good social engineering and it is up to the IT department to make users aware of when this might be going on in order to prevent it from happening. One interesting attack, although this was, I am convinced, said quite innocently, came from a conversation recently when I was signing up to a service. I was asked for a password and the operator suggested :"how about one that you already use?" This opens up a goldmine for root password harvesting, online bank account passwords and so on. Needless to say that I made up a new one. |
HelpDesk Extra
Simplified and OSI StackTCP/IP StackThis is the simplified stack model that some people refer to.
OSI StackYou can see the parallels between the 5 layer stack and the OSI stack below. When firewalls refer to layer '4 technology' or 'layer 7', they are nearly always referring to the OSI model.
|
||||||||||||||||||||||||||||||||||||||||||
Packet structureYou can see how the data is added to - although not necessarily by every layer - so that by the time it reaches the copper wire, the data part of the packet has shrunk in proportion. In this way, that 100Mbps LAN of yours cannot carry 100Mbps of data (even if there were no packet collisions or bottlenecks elsewhere.
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Tools
The screenshot on the right comes from the tools pages
of the SonicWALL firewall (the Tele3 TZX to be precise) Of course, you are not limited to looking up the names
or IP addresses of hosts that have apparently attacked
you, you can type in your favourite URLs and see what
they are.
Here, compuserve's homepage server's address goes into the address line of Internet Explorer and it displays the same web page. However, this is not always the case as each server is
not limited to having just a single domain name. |
Dual- and Tri-Homed firewalls
The green traffic is traffic that is considered all
right whereas the red traffic on the diagram is unknown
or hostile. In keeping with the ancient tradition of all
Internet diagram drawing, the Internet (PFC) is a Pink
Fluffy Cloud. A tri-homed firewall has three NICs
and therefore, there are three potential paths so the
logical Above you can see the diagram for a tri-homed fireall. This one also has a VPN that allows corporate data to travel directly from home to company and vice-versa. Having the home network and the work machine at home separated by a firewall means that you can block all traffic from the home network or allow just https (secure http using SSL (Secure Socket Layer)) to manage the firewall. One thing you can do still is to print to the network computer as traffic is allowed into the home network that originates from the work machine. Of course, if you have one of these at home and a fast (1Mbps +) connection, you might consider that your secured home network can go on one internal NIC and the other internal NIC can go to a WLAN thus providing a hotspot in your street (and for around 300+ metres around). You can control the data flowing through using various filters so you can avoid a scenario where people are downloading the wrong type of material but I am sure that the neighbours would find it useful. |
VPNs
If, instead of just a work machine, you had a home network, this might happen as a result of browsing so it is best to separate any home related activities from the work machine at home
|
Network Topologies - 'Dangerous' and 'Safer'If you have just one computer connected to your Internet connection then as a minimum, you should have a desktop firewall to protect it - remember that these are not running on a dedicated system with a hardened operating system. (A hardened operating system is one that has had all unnecessary processes removed and those remaining have been tightened up in a security sense - buffer overruns taken care of and so on.) Dangerous
If you go in through the computer with the desktop
firewall on it (such as through a USB interface on the
broad/ISDN modem), you are still running a firewall on an
O/S that is not hardened. Also, you are dependent upon
the machine with the firewall on it being up and running
all of the time and doing little else - additional
services/programs mean additional risks. One tempting
thing is to use the LAN connection on the modem but
unless you are going to plug it directly into your LAN,
you still have the same problem as with the USB. Even more dangerous
Supposing somebody decides to look around your system - there is nothing that you can do to stop them. They can perform port scans on your machines, get your machines to identify which O/S they use and with that information they can test them for vulnerabilities if you are not up to date with patches. If you still have your desktop firewall on your first machine, it will be as protected as it was before but you will have to install another desktop firewall on the second computer and any other computer that comes onto the network. You will also have to keep them all up to date. In addition to this, your ISP will be probing your
network to see how many machines there are and they will
all want an address from the ISP's DHCP Server so you
will need to configure everything to be a DHCP client. If
you have enough hosts to go over your ISP's limit your
will be in trouble. Further to this, your network printer
will now have an Internet addressable IP address (as
opposed to a private one on your LAN) so somebody in
Chile or New Zealand can use up your printer resources
(it will also have its own web page as that is how you
configured it). Safer
|
 Broadband goes into a
marshalling box similar to this one, via optical cable
and is sent to your home on a 666MHz carrier to your
cable modem where it ends up as an ethernet data source
or USB at 150kbps, 512kbps, 600kbps or over 1Mbps
depending on the service you have subscribed to. What you
do with it then is up to you.
Broadband goes into a
marshalling box similar to this one, via optical cable
and is sent to your home on a 666MHz carrier to your
cable modem where it ends up as an ethernet data source
or USB at 150kbps, 512kbps, 600kbps or over 1Mbps
depending on the service you have subscribed to. What you
do with it then is up to you.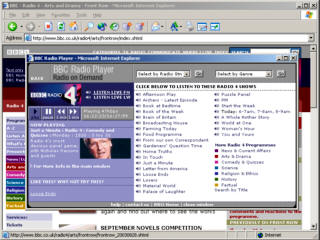 Unless
you are into playing games, shifting large files around
the Internet, or have an attention span of less than
three seconds (waiting for a page to download - similar
to a goldfish's attention span) you are fairly limited to
what you can do with it. Listening to streaming media
such as radio from the BBC or other services might be all
that it is practical for in some instances. At least with
POTS (Plain Old Telephone Service) it was only on when
you wanted it and with a limited bandwidth, people
downloading large files from your system would have been
noticed.
Unless
you are into playing games, shifting large files around
the Internet, or have an attention span of less than
three seconds (waiting for a page to download - similar
to a goldfish's attention span) you are fairly limited to
what you can do with it. Listening to streaming media
such as radio from the BBC or other services might be all
that it is practical for in some instances. At least with
POTS (Plain Old Telephone Service) it was only on when
you wanted it and with a limited bandwidth, people
downloading large files from your system would have been
noticed. Firewalls offer some
interesting tools to help you find things out - either
for the purpose of users genuinely finding out what is
going on or, for the morbidly curious.
Firewalls offer some
interesting tools to help you find things out - either
for the purpose of users genuinely finding out what is
going on or, for the morbidly curious.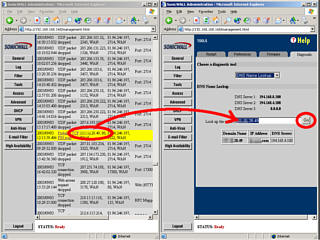 domain name of the IP
address that has apparently attacked your computer (it
might just be a trojan on somebody's machine and they are
not aware of it, rather than somebody sitting up at night
in their bedroom, trying to break into your computer
network), you can open up another administrator browser
and simply drag the IP address and drop it into the DNS
lookup box.
domain name of the IP
address that has apparently attacked your computer (it
might just be a trojan on somebody's machine and they are
not aware of it, rather than somebody sitting up at night
in their bedroom, trying to break into your computer
network), you can open up another administrator browser
and simply drag the IP address and drop it into the DNS
lookup box.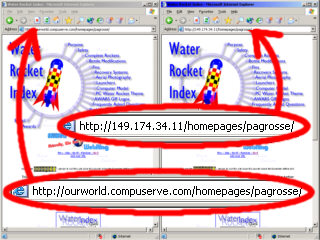 The following is all
information that you can get using sites on the Internet
- go into Google and search for 'reverse DNS lookup'.
The following is all
information that you can get using sites on the Internet
- go into Google and search for 'reverse DNS lookup'.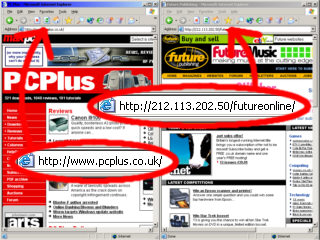 Here, the PC Plus
website gives you the PC Plus home page when you type the
name in but if you type in the IP address instead, the
server doesn't know which website you are interested in
so it uses the default that it is assigned under these
circunstances and transfers you to the futureonline page.
Here, the PC Plus
website gives you the PC Plus home page when you type the
name in but if you type in the IP address instead, the
server doesn't know which website you are interested in
so it uses the default that it is assigned under these
circunstances and transfers you to the futureonline page.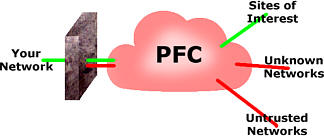 A dual-homed
firewall has two Network Interface Cards (NICs) and, as
there is only one path between them, there is only one
firewall.
A dual-homed
firewall has two Network Interface Cards (NICs) and, as
there is only one path between them, there is only one
firewall.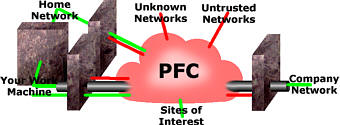 solution is to have
three firewalls. Many years ago, this was not always the
case but no manufacturer would last long nowadays if
there was only a partial firewall between the Internet
and the DMZ and the DMZ and the LAN.
solution is to have
three firewalls. Many years ago, this was not always the
case but no manufacturer would last long nowadays if
there was only a partial firewall between the Internet
and the DMZ and the DMZ and the LAN.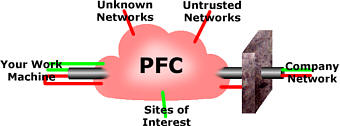 This is what happens
if you have just a VPN without a firewall at the remote
end. Hostile traffic can invade the remote end's machine
and get into the VPN where it can gain access to the
corporate network unhindered by a firewall.
This is what happens
if you have just a VPN without a firewall at the remote
end. Hostile traffic can invade the remote end's machine
and get into the VPN where it can gain access to the
corporate network unhindered by a firewall.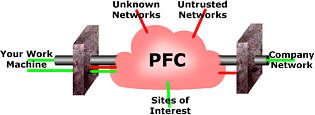 With a firewall
protecting the remote machine, untrusted and hostile
traffic is prevented from entering the VPN. However, it
cannot protect against malicious software that has gained
access legitimately to the remote machine then looking
through the VPN.
With a firewall
protecting the remote machine, untrusted and hostile
traffic is prevented from entering the VPN. However, it
cannot protect against malicious software that has gained
access legitimately to the remote machine then looking
through the VPN.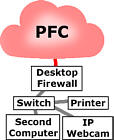 However, you might
have your own network with, say, a switch, two computers,
a network printer and an IP webcam (a proper webcam that
goes directly into the LAN, not the sort that you plug
into your computer).
However, you might
have your own network with, say, a switch, two computers,
a network printer and an IP webcam (a proper webcam that
goes directly into the LAN, not the sort that you plug
into your computer).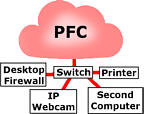 Let's see what
happens with it plugged into the LAN. Traffic from the
Interent, from people on the local network (people on the
same service provider in your area) all burden your LAN
with traffic, clogging up your printer server and
interfering with the live stream from your IP webcam. It
gets worse.
Let's see what
happens with it plugged into the LAN. Traffic from the
Interent, from people on the local network (people on the
same service provider in your area) all burden your LAN
with traffic, clogging up your printer server and
interfering with the live stream from your IP webcam. It
gets worse.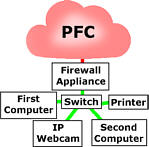 If you put a firewall
between your switch and the modem you can stop this
traffic from getting into your network in the first place
so all of those lights on your system only flash when you
are doing something.
If you put a firewall
between your switch and the modem you can stop this
traffic from getting into your network in the first place
so all of those lights on your system only flash when you
are doing something.